Introduction to Quantum Computing
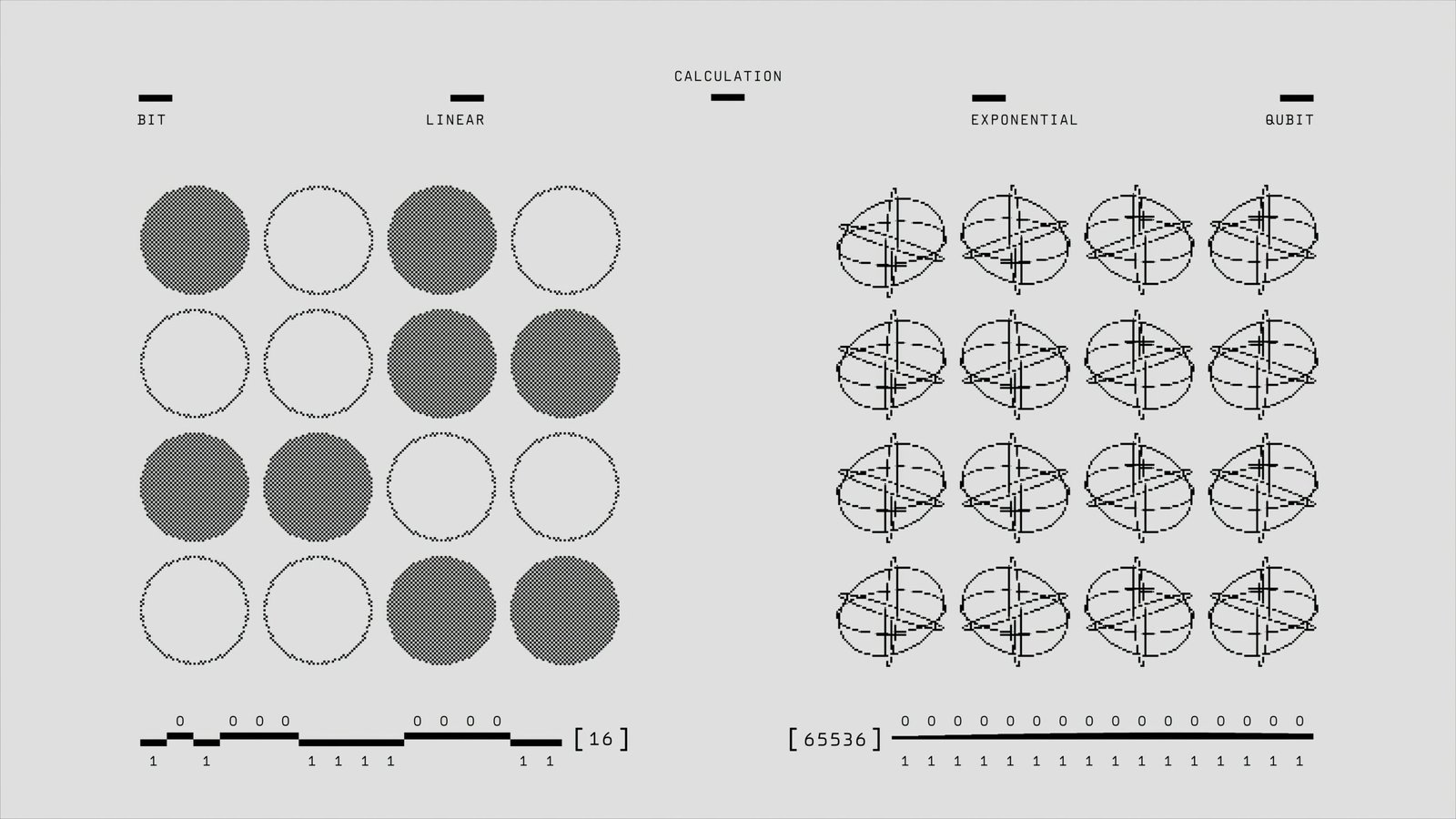
Quantum computing represents a groundbreaking advancement in the field of information technology, distinguished from classical computing by its fundamental operating principles. At its core, quantum computing harnesses the unique behaviors of quantum mechanics, employing quantum bits, or qubits, which differ significantly from the binary bits used in classical systems. While classical bits can exist in one of two states—either a 0 or a 1—qubits exploit the phenomena of superposition and entanglement, allowing them to exist in multiple states simultaneously.
Superposition is a defining feature of quantum computing, enabling qubits to represent both 0 and 1 at the same time. This characteristic exponentially increases the processing power of quantum computers, allowing them to perform complex calculations far more efficiently than traditional computers. For instance, a quantum computer with just a few qubits can process vast amounts of data simultaneously, surpassing the capabilities of even the most advanced classical supercomputers.
Entanglement, another crucial principle of quantum mechanics, forms a robust link between qubits. When qubits become entangled, the state of one qubit is directly related to the state of another, regardless of the distance between them. This feature offers unprecedented advantages in quantum computing, particularly in enhancing speed and security. These properties not only differentiate quantum computers from their classical counterparts but also provide unique opportunities for applications in various fields, including cybersecurity.
Understanding these foundational elements of quantum computing is essential, as they set the stage for exploring how this innovative technology can address pressing challenges in cybersecurity. With its potential to revolutionize data protection measures, quantum computing stands at the forefront of technological advancements that aim to safeguard sensitive information in an increasingly digital world.
Current Challenges in Cybersecurity
The landscape of cybersecurity is fraught with challenges, as cyber threats continue to evolve at an alarming rate. One of the most pressing issues is the sophistication of these threats. Cyber attackers are becoming increasingly skilled, employing advanced techniques that can circumvent traditional security measures. This escalation necessitates a paradigm shift in how organizations approach their cybersecurity strategy, highlighting a critical need for innovative solutions.
Another significant challenge lies within the limitations of current encryption methods. Traditional encryption techniques, while effective against simpler attacks, are increasingly insufficient in the face of more complex threats. As computational power advances, classic cryptographic approaches are being rendered vulnerable. Hackers can leverage modern computing capabilities to break conventional encryption, which raises serious concerns about data integrity and confidentiality. This reality underscores the urgency for more resilient forms of data protection, as organizations find their sensitive information increasingly at risk.
Moreover, the growing reliance on digital platforms across various industries has amplified the demand for robust security solutions. Businesses must secure their operations against a backdrop of ever-globalizing threats, where vulnerabilities in one sector can have cascading effects throughout connected systems. The sheer volume and variety of devices connected to the internet exacerbate this issue, requiring a comprehensive strategy to safeguard these environments from compromise. In this context, cybersecurity cannot remain static; rather, it must adapt to new threats and utilize emerging technologies to bolster defenses.
Together, these challenges paint a picture of an urgent need for innovation in cybersecurity. As the field grapples with increasing sophistication among cyber adversaries and weaknesses in existing protections, it becomes paramount to explore advanced solutions. The advent of quantum computing holds promise in addressing these challenges, offering the potential for unprecedented advancements in secure communication and data protection.
Understanding the Mechanics of Quantum Computing
Quantum computing is a revolutionary approach to information processing that leverages the principles of quantum mechanics. Unlike classical computers, which use bits as their basic unit of information (0s and 1s), quantum computers use quantum bits or qubits. A qubit can exist in multiple states simultaneously, thanks to the principle of superposition. This unique property allows quantum computing to perform complex calculations much faster than traditional methods.
In addition to superposition, quantum entanglement plays a crucial role in the functionality of quantum computers. When qubits become entangled, the state of one qubit instantly influences the state of another, regardless of the distance separating them. This interconnectedness enables quantum algorithms to process vast amounts of data concurrently, significantly enhancing computational power. Quantum algorithms are designed to exploit these properties, leading to potentially groundbreaking solutions for problems that are currently infeasible for classical computers.
One prominent application of quantum computing is in the realm of cybersecurity, particularly through quantum key distribution (QKD). QKD utilizes the principles of quantum mechanics to create a secure communication channel between two parties. By encoding information in quantum states, any attempt to intercept or eavesdrop on the key will disturb the system, alerting the users to potential security breaches. This characteristic makes QKD inherently secure compared to classical cryptographic methods, which can be vulnerable to various hacking techniques.
The advancement of quantum computing heralds a new era for cybersecurity by potentially rendering traditional encryption methods outdated. As research progresses, the integration of quantum algorithms into secure communications is likely to redefine how data privacy and security are maintained in an increasingly digital world. The implications of this technology extend beyond enhanced security; they promise to revolutionize various fields, including finance, healthcare, and beyond.
Quantum Cryptography: A Game Changer
Quantum cryptography represents a groundbreaking advancement in secure communication, leveraging the principles of quantum mechanics to surpass the limitations of classical cryptographic methods. At its core, quantum cryptography utilizes phenomena such as superposition and entanglement to create secure keys, which are essential for encrypting information. This innovative approach not only enhances the security of data transmission but also provides a mechanism for detecting potential eavesdropping attempts, a critical aspect when considering cybersecurity.
One of the most notable advantages of quantum cryptography is its resistance to hacking. In traditional encryption methods, keys can be intercepted and potentially exploited, leading to vulnerabilities in data protection. However, through quantum key distribution (QKD), any attempt to measure a quantum system inevitably alters its state, thereby alerting the communicating parties of potential intrusions. This ensures that any communicated information maintains a higher degree of confidentiality and integrity compared to conventional methods.
Furthermore, quantum cryptography offers the potential for unbreakable encryption through the use of quantum states. Unlike classical systems, where computational power can be used to decrypt information, the unique properties of quantum systems render these keys secure against even the most advanced algorithms. As quantum computing technology evolves, the need for robust security measures becomes increasingly paramount. Quantum cryptography serves as a proactive response to this challenge, positioning itself as an essential tool in the cybersecurity landscape.
In light of these advantages, organizations and institutions are beginning to explore the integration of quantum cryptography into their security frameworks. Embracing this cutting-edge technology not only empowers stakeholders to bolster data security but also sets a new standard in the fight against cyber threats. As quantum computing continues to develop, so too does the importance of incorporating quantum cryptographic protocols into modern cybersecurity practices.
Potential Threats: Quantum Computing and Cryptanalysis
Quantum computing presents a unique set of challenges to the field of cybersecurity, particularly concerning encryption standards that currently safeguard sensitive information. Traditional encryption methods, such as RSA and ECC (Elliptic Curve Cryptography), form the backbone of data security in communication channels, online transactions, and personal information protection. However, the advent of quantum algorithms, particularly Shor’s algorithm, poses a significant threat to these established frameworks.
Shor’s algorithm is specifically designed to efficiently factor large integers, thereby undermining the security of RSA encryption, which relies on the computational difficulty of this factorization. In a post-quantum world, an adversary equipped with a sufficiently powerful quantum computer could theoretically decrypt encrypted communications almost instantaneously, rendering many currently utilized encryption methods obsolete. This quantum advantage emphasizes an urgent need for a strategic overhaul of cybersecurity measures and the transition to post-quantum cryptography solutions.
Additionally, the ramifications of quantum computing extend beyond just encryption breaking; they also involve the integrity and authenticity of digital signatures. Algorithms employed for digital signatures are critical for assuring the legitimacy of communications and transactions. Quantum capabilities could enable attackers to forge signatures, leading to potential financial and data breaches that traditional methods cannot effectively counter. Thus, as quantum computing technologies advance, the necessity for robust cryptographic alternatives becomes increasingly pertinent.
The cybersecurity landscape is on the brink of a paradigm shift necessitating proactive measures. Organizations and institutions must invest in research and development of quantum-resistant algorithms and engage in dialogues about the future of cybersecurity mechanisms. As we continue to explore the emerging world of quantum technologies, safeguarding sensitive data against potential quantum threats must become a priority.
The Transition to Quantum-Resistant Cryptography
The advent of quantum computing presents new challenges for the field of cybersecurity, particularly concerning cryptography. Conventional cryptographic methods, such as RSA and ECC (Elliptic Curve Cryptography), rely on the computational difficulty of certain mathematical problems. However, quantum computers possess the capability to solve these problems exponentially faster than classical computers, essentially rendering traditional encryption methods obsolete. This necessitates a shift toward quantum-resistant cryptography, which is specifically designed to withstand potential attacks from quantum-enabled adversaries.
Quantum-resistant cryptographic algorithms are fundamentally different from classical approaches. They utilize mathematical structures that are believed to be secure against the threats posed by quantum computing. Examples of such algorithms include lattice-based cryptography, hash-based signatures, and multivariate polynomial cryptography. These cryptographic techniques aim to provide a robust framework capable of resisting both current and future quantum attacks, ensuring the integrity and confidentiality of sensitive data.
Ongoing efforts to develop and standardize quantum-safe encryption techniques are critical for our digital future. Leading organizations, including the National Institute of Standards and Technology (NIST), have initiated a comprehensive process to evaluate and select post-quantum cryptographic algorithms. This initiative represents a significant milestone towards establishing a new cryptographic standard that can secure information against quantum threats. The chosen algorithms will undergo rigorous testing and validation before being adopted into mainstream usage, providing a significant degree of security for governmental, financial, and private organizations.
As we transition to a future increasingly influenced by quantum technology, proactive measures in updating cryptographic systems are essential. Organizations must begin researching and implementing quantum-resistant methods as part of their cybersecurity strategy. Adapting to these changes ensures that critical information remains protected, safeguarding against the potential ramifications of quantum computing-driven vulnerabilities.
Case Studies: Quantum Computing in Action
As industries continue to seek robust solutions for cybersecurity, several companies are leveraging quantum computing technologies to enhance their security frameworks. One notable example is IBM, which has been at the forefront of quantum cryptography. IBM’s Quantum Network allows businesses to experiment with quantum-safe algorithms on their quantum computers, permitting companies to explore the ramifications of quantum computing for data security. Through their efforts, organizations gain insights into how quantum technology can evolve current encryption methods to protect sensitive data against potential quantum attacks.
Another significant player is Google, which has explored the use of quantum algorithms for encryption and key distribution. Their recently published research highlights the potential for quantum key distribution (QKD) systems to provide unbreakable encryption by using quantum mechanics principles. By implementing QKD in real-world situation scenarios, such as reinforcing communications in critical infrastructures, Google’s efforts illustrate the practical safety that quantum technologies can bring in contrast to current classical systems.
In the finance sector, Bank of America is actively investigating quantum computing’s capabilities for securing transactions and reducing fraud. By utilizing hybrid encryption techniques that include quantum elements, they aim to enhance the security of sensitive financial data shared across networks. Their experiments focus on tracking the effectiveness of quantum encryption in real-world banking applications, where the security of customer data remains a top priority.
Moreover, startups such as ID Quantique are pioneering advancements in quantum random number generation which is essential for cryptographic applications. These innovations provide secure keys that are more resistant to eavesdropping compared to traditional random number generators, thereby laying a foundation for reliable cybersecurity infrastructures in various sectors.
These cases underscore the transformative potential of quantum computing in the cybersecurity landscape, affirming its role as a pivotal technology in counteracting emerging cyber threats.
The Future of Cybersecurity in the Quantum Era
The advent of quantum computing heralds a significant shift in the cybersecurity landscape, necessitating a re-evaluation of existing protocols and strategies. As quantum technologies evolve, their implications for secure communications and data protection become increasingly profound. Current encryption methods, predominantly based on classical computing, are at risk of being compromised by the processing power offered by quantum systems. Consequently, the future of cybersecurity must focus on developing quantum-resistant algorithms that can withstand the capabilities of these innovative computing technologies.
Emerging technologies will play a crucial role in addressing the challenges posed by quantum computing. For instance, quantum key distribution (QKD) offers a promising avenue for secure transmission of information. By utilizing the principles of quantum mechanics, QKD ensures that any attempt to intercept the message results in detectable alterations, thereby maintaining the integrity of data. Researchers and organizations must prioritize investment in such technologies in order to establish a robust defense against potential breaches orchestrated through quantum attacks.
Moreover, the landscape of cybersecurity in the quantum era will likely be shaped by changes in policies and regulations. Governments and regulatory bodies will need to implement frameworks that encourage the adoption of quantum-safe practices while fostering international collaboration among cybersecurity experts. These initiatives could facilitate knowledge sharing and best practices, thus enhancing global defense mechanisms against cyber threats reinforced by next-generation computing power.
Collaboration among academia, industry, and governments is paramount to bridge the gap between quantum advancements and practical cybersecurity applications. By leveraging collective expertise, stakeholders can develop innovative methodologies that ensure secure environments for both individuals and organizations. In approaching these challenges proactively, the cybersecurity domain can effectively position itself to adapt and thrive in the era of quantum computing.
Conclusion: Embracing Quantum Solutions for a Safer Tomorrow
As the digital landscape continues to evolve, the importance of robust cybersecurity measures cannot be overstated. The growing complexity of cyber threats necessitates a paradigm shift in how organizations approach security. Quantum computing represents a pivotal advancement in this context, offering unprecedented capabilities that can enhance our defenses against malicious attacks and safeguarding sensitive data. Throughout this discussion, we have explored how quantum technologies can revolutionize the cybersecurity sector, from their potential to break traditional encryption methods to their ability to create new, quantum-based encryption protocols.
One of the most significant implications of quantum computing is its capacity to perform calculations at speeds far beyond the capabilities of classical computers. This not only enables the rapid assessment of potential vulnerabilities but also facilitates the development of more secure cryptographic systems. Furthermore, quantum key distribution (QKD) exemplifies how these technologies can ensure that communication remains secure from eavesdroppers, a vital concern for individuals and organizations alike.
However, with the advent of quantum capabilities also comes an urgent need for organizations to prepare for the inevitable transition. Stakeholders must invest in research and development to understand the intricacies of quantum computing better and its impacts on existing cybersecurity frameworks. Moreover, integrating quantum solutions into current systems will require collaboration across industries and a commitment to continuous learning as the field evolves rapidly.
In conclusion, embracing the power of quantum computing is not merely a choice but an essential step toward a safer digital future. As cyber threats grow increasingly sophisticated, it is imperative that organizations remain informed and proactive in adapting to the changes that quantum technologies bring. By doing so, they can better protect themselves and their data in an ever-changing cybersecurity landscape.
